Digital banking for business
Seamlessly access all of your accounts from one place with First Citizens Digital Banking for business.
With an increase in remote work, companies using third-party cloud solutions with unforeseen security vulnerabilities and gaps in cyber-awareness among employees, it's more important than ever to have a cybersecurity plan in place.

While today's cybersecurity threats aren't much different from those in the past, hackers are now using more sophisticated means—including AI—to automate how they attack devices and systems. Here's what you need to know as you create your own cybersecurity plan.
Before creating a cybersecurity plan for your small business, it's important to know the top cybersecurity threats facing most companies today. The following are considered cyberattacks, or external breaches by hackers with a goal of exposing or deleting sensitive information.
There are four common types of cyberattacks.
Increased usage of cloud solutions may also open your business to more types of cybersecurity threats, especially if you don't have strong endpoint security. Cloud solutions store and transmit data on virtual servers, which may give hackers an easier entry point compared to a physical server—especially if the provider you're using doesn't practice strong enterprise security.
While these threats exist, there are ways to protect your business. Use the strategies below to create your plan, and view the National Institute of Standards and Technology's list of free and low-cost cybersecurity training resources to help build company-wide awareness of the importance of having a cybersecurity plan.
Cloud-monitoring tools can watch out for activity on your network and send alerts when there's something suspicious. Some types can even isolate these threats from your network so hackers can't access sensitive information.
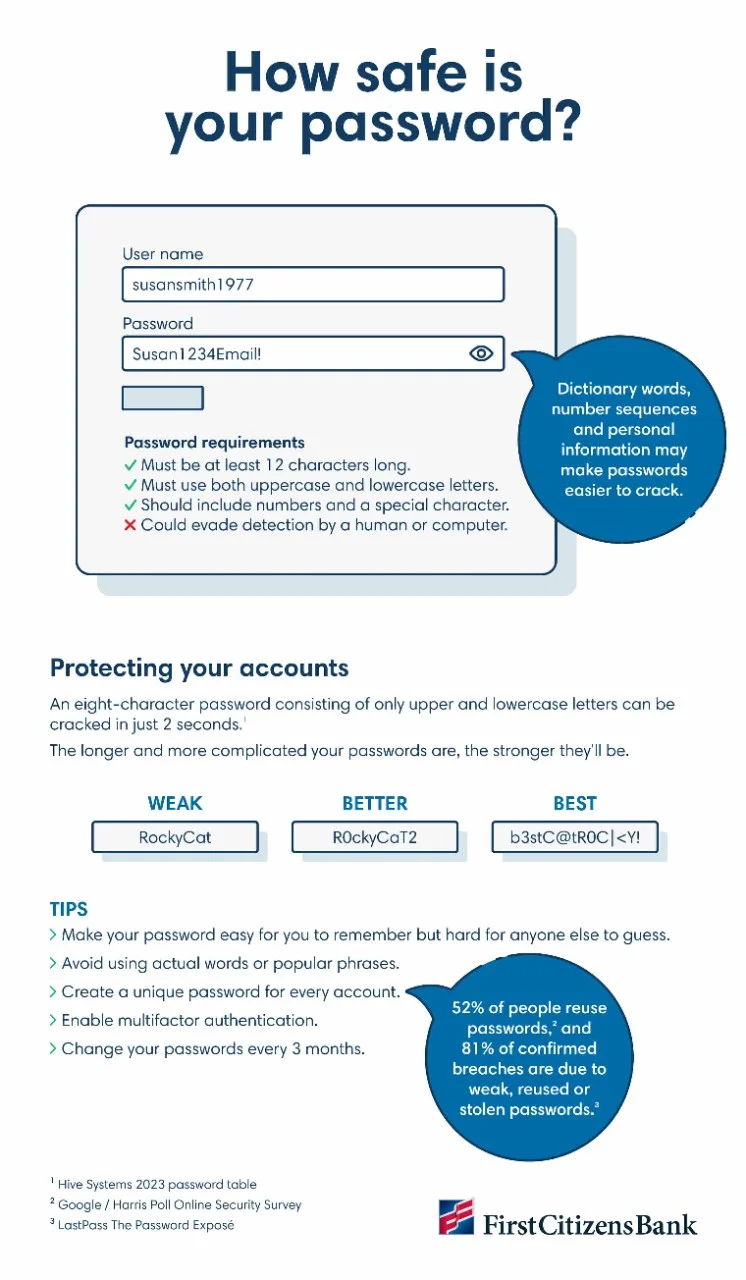
Keep all computer systems, software applications and devices up to date, and ensure everything is protected by a password. Also make sure you and your employees use passwords that are complex, unique and difficult to guess. Change usernames, logins and passwords every 90 days, and use a secure password manager app to store them.
Often considered the first line of cybersecurity defense, firewalls block incoming traffic and network requests originating from malware or unsecured sites. All hardware and software—including payment terminals, smartphones and tablets—should have the most up-to-date firewall software, as well as antivirus and anti-malware software. Also consider using a virtual private network, or VPN, for additional network encryption—especially if your business has remote employees.
Set a schedule that includes daily backups of important business data and transactions onto a separate hard drive, server or the cloud for an additional layer of protection. Also determine if you need separate networks and authentication processes for your payment terminal and the rest of your business operations, as well as network monitoring to detect unusual activity.
Consider adding a layer of protection with two-factor authentication. Many financial institutions and online payment services have settings that allow you to authenticate your account activity by entering a single-use code that's sent to your phone or email. You can also request text alerts from your bank to notify you of any suspicious activity, including whenever your email address is changed or your login and password are reset.
When employees send confidential data to each other, make sure they encrypt the information so it's more difficult to steal. They should also avoid sending data using public Wi-Fi networks and should instead only use your company's secured network.
Don't let third-party vendors access systems with private data unless it's essential. The same applies to employees. Limit access to data wherever possible.
For additional support, consider hiring a cybersecurity consultant for advice on how to prevent a data breach, especially if your business doesn't have its own in-house IT team.
Cybersecurity insurance can help protect your business against significant financial damage from technology-related crimes.
Businesses of any size can implement technology to protect themselves, but these systems and processes are only as good as the people who use them. Your employees are the front-line responders who are most likely to deal directly with cybercriminals, so they should all be included and active participants in your cybersecurity incident response plan.
Make sure employees are aware of the threats and security measures you've put in place, and give them clear directions for how to report suspicious activity—no matter how seemingly small or innocent. Hold training sessions regularly so the message sticks, and make your cybersecurity plan for small business available to all team members. All it takes is one downloaded attachment from an untrusted source to cause serious problems.
As more organizations digitize their operations, cybersecurity threats will continue to increase. Implement these best practices so you can reduce your risk—and protect your business.
Email Us
Please select the option that best matches your needs.
Customers with account-related questions who aren't enrolled in Digital Banking or who would prefer to talk with someone can call us directly.